Identity and access management plays a crucial role in securing an organizations’ information and assets. We adopt an integrated approach identity and access management and develop customized IAM frameworks that not only provide a roadmap for prioritizing specific areas to reduce risks but also are scalable for your evolving business requirements.
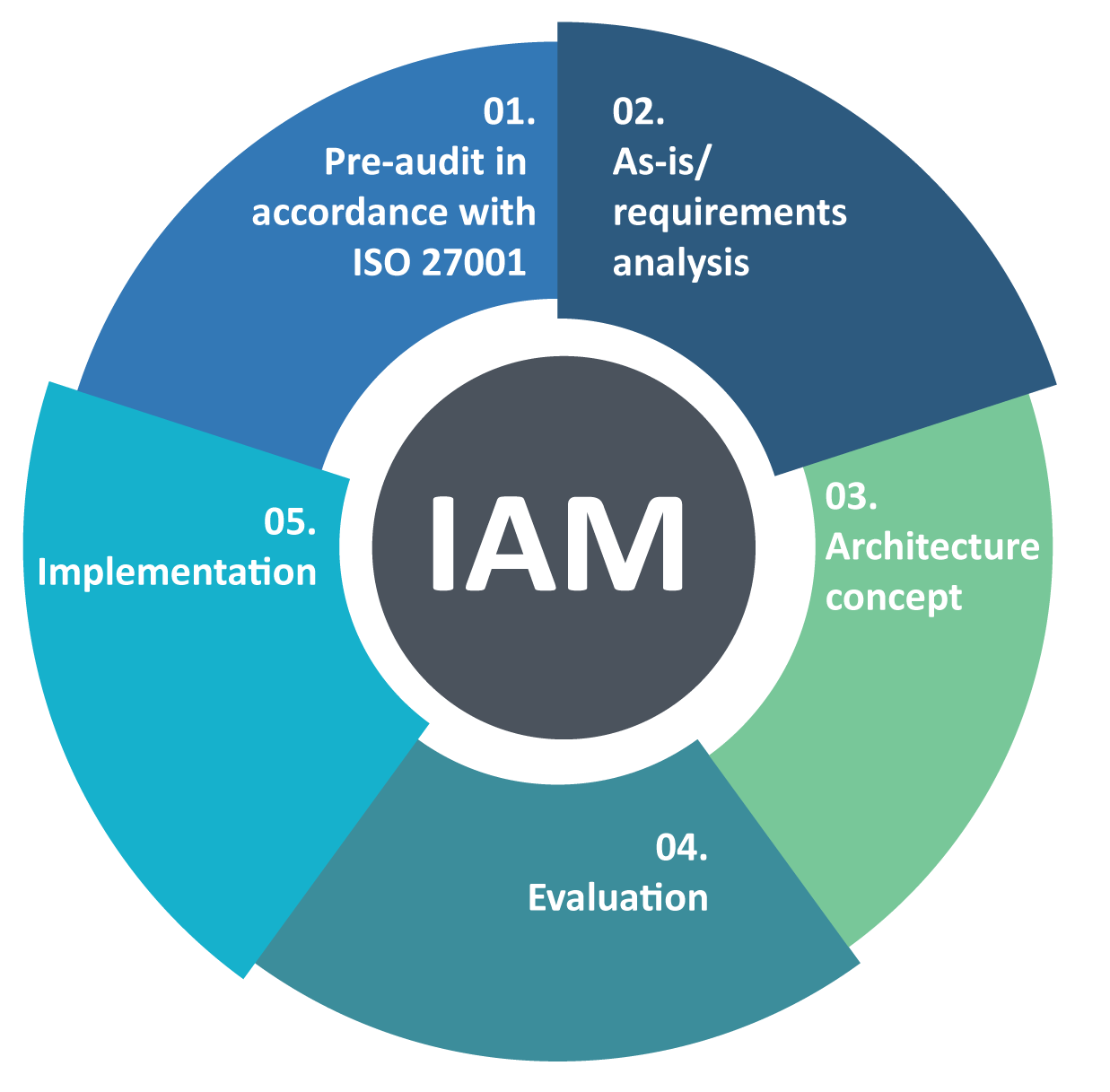
Securing an identity is inevitable for every business transaction, internally for employees and externally for users, vendors and suppliers. Identity and access management plays a crucial rule in securing organisation's information and assets by ensuring that authorised people have right level of access to the information or assets. With ever evolving technology, managing a users identity on multiple platforms and ensuring that authorised users have right access rights to their resources based on 'need-to-know' has become complex and difficult. At SecureLink, we understand technology, regulations and your organisational requirements. We follow an integrated approach to manage internal and external identity and access management and develop customised IAM frameworks that not only provide roadmap for prioritizing specific areas to reduce risks but also are scalable for your evolving business requirements.

